The complexity of hacks – A case study
The complexity of hacks – where and why are they doing it?
A poor client was repeatedly getting his site hacked. All the usual methods were carried out several times. In the end, we resolved it was a theme hole, and probably a hacked database and a new site was rebuilt for him, identical in looks and content, but totally clean.
A few days before we replaced it I had some time, so I went really looking, following lots of reading and low and behold. Found a back door. After so many hours and so many file inspections, visitor logs, I was furious. Then, I really started to look.
Here is the hack url //wp-includes/pomo/index.php, the pomo folder was hacked and a replacement index page was loaded, with a nice easy upload any file anywhere button.
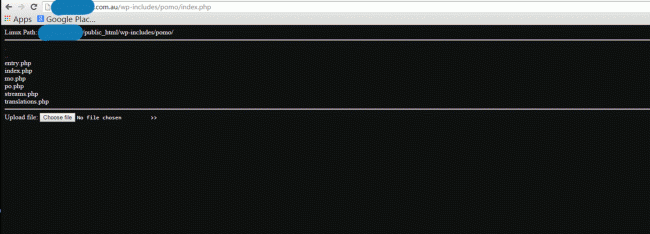
Then I was angry, so I set an ambush, I was going to find these buggers. Replacement page built, removed the upload function and kept the page live. Then I put in a nice little bit of text to say hello to visitors to that page LOL, and put in some analytics code from a redundant website and set to watch live traffic in analytics. With that, had server logs open and went about my daily business.
Then I got thinking and did a Google search for the folder string and low and behold look what I found indexed on Twitter?
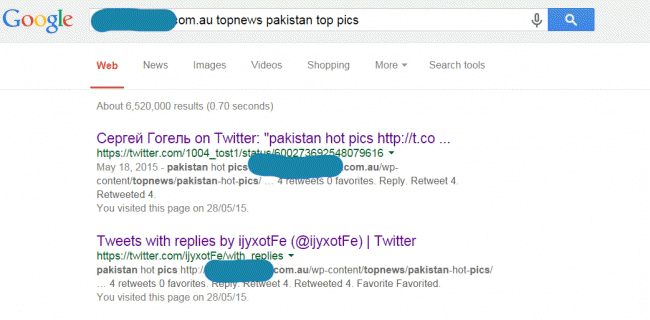
So, I started researching the old mate who was sharing his “work” on twitter with his mates in russia, and then I found the resulting referral page that was receiving the traffic from the hack, very interesting. Then, strangely, on the old hack page a large and consistent stream of visitors, all from the same domain.
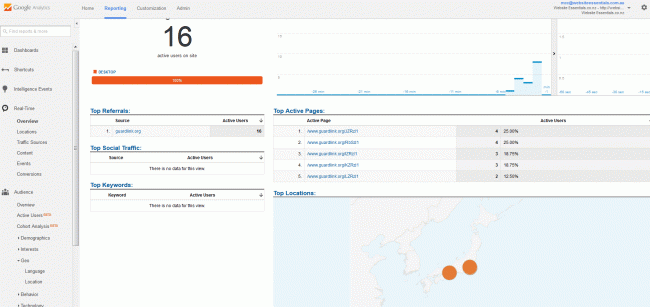
Ghost visits from a lovely mob in Japan known as guardlink.org. They also apparently do some nice work from pornhub and a few other domains. Then it tweaked, I had a client last week that I saw some of these ghost visits in analytics (interestingly these visits do now show up in your server visits logs, but are hacked analytics codes I think in other sites pages or links)
The only way these immediate visitors to the RECONSTRUCTED page, recorded in their systems, could have been triggered immediately after I visited that main linked page from the twitter account reference, that the clients site that had the topnews hack referring to. Then as a test, remembering the other site the other week I turned on analytics real time, visited the old porn hub link and bingo, the ghost visit and then good old guard link started to fire off.
So here I am now off to find the hack in the site from the other site from the other week. I will let you know what I find… And, hosting and security is now not just serious, its bloody serious, because it now affects your analytics and maybe your rankings, more to follow…

